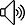! boot.s
!
! It then loads the system at 0x10000, using BIOS interrupts. Thereafter
! it disables all interrupts, changes to protected mode, and calls the
BOOTSEG = 0x07c0
SYSSEG = 0x1000 ! system loaded at 0x10000 (65536).
SYSLEN = 17 ! sectors occupied.
entry start
start:
jmpi go,#BOOTSEG
go: mov ax,cs
mov ds,ax
mov ss,ax
mov sp,#0x400 ! arbitrary value >>512
! ok, we've written the message, now
load_system:
mov dx,#0x0000
mov cx,#0x0002
mov ax,#SYSSEG
mov es,ax
xor bx,bx
mov ax,#0x200+SYSLEN
int 0x13
jnc ok_load
die: jmp die
! now we want to move to protected mode ...
ok_load:
cli ! no interrupts allowed !
mov ax, #SYSSEG
mov ds, ax
xor ax, ax
mov es, ax
mov cx, #0x2000
sub si,si
sub di,di
rep
movw
mov ax, #BOOTSEG
mov ds, ax
lidt idt_48 ! load idt with 0,0
lgdt gdt_48 ! load gdt with whatever appropriate
?
! absolute address 0x00000, in 32-bit protected mode.
mov ax,#0x0001 ?! protected mode (PE) bit
lmsw ax ! This is it!
jmpi 0,8 ?! jmp offset 0 of segment 8 (cs)
gdt: .word 0,0,0,0 ! dummy
.word 0x07FF ! 8Mb - limit=2047 (2048*4096=8Mb)
.word 0x0000 ! base address=0x00000
.word 0x9A00 ? ! code read/exec ?代碼段,1001 1010 0000 0000 ,S標志位置1(數據段或代碼段)
.word 0x00C0 ! granularity=4096, 386
.word 0x07FF ! 8Mb - limit=2047 (2048*4096=8Mb),粒度為4k
.word 0x0000 ?! base address=0x00000
.word 0x9200 ! data read/write ? 1001 ?0010 0000 0000,注意每一位是干什么用的,運行在特權級0,S標志位置1(數據段或代碼段),擴展方向
.word 0x00C0 ? ! granularity=4096, 386
idt_48: .word 0 ! idt limit=0
.word 0,0 ! idt base=0L
gdt_48: .word 0x7ff ? ?! gdt limit=2048, 256 GDT entries
.word 0x7c00+gdt,0 ? ? ?! gdt base = 07xxx
.org 510
.word 0xAA55
?
更多文章、技術交流、商務合作、聯系博主
微信掃碼或搜索:z360901061

微信掃一掃加我為好友
QQ號聯系: 360901061
您的支持是博主寫作最大的動力,如果您喜歡我的文章,感覺我的文章對您有幫助,請用微信掃描下面二維碼支持博主2元、5元、10元、20元等您想捐的金額吧,狠狠點擊下面給點支持吧,站長非常感激您!手機微信長按不能支付解決辦法:請將微信支付二維碼保存到相冊,切換到微信,然后點擊微信右上角掃一掃功能,選擇支付二維碼完成支付。
【本文對您有幫助就好】元